1 DRM system Digital Rights Management (DRM) is a way to protect multimedia content from unauthorized playback and reproduction. DRM technology protects digital content by encrypting and attaching usage rules to digital content, where rules can be used to determine whether a user is eligible to play digital content, thereby preventing content from being copied or limiting the number of times the content is played. The operating system and multimedia are responsible for enforcing these rules. The simple structure of DRM can be represented by the following figure.
This article refers to the address: http://

The DRM implementation process consists of the following basic work steps: the content delivery process, the content packaging process, the content release process, and the process of obtaining content usage licenses.
First, the user needs to apply for or subscribe to the video program that needs to be viewed from the content server, and the content sender will package the content, and send the content packaging process, including compression and encryption processing of the content file. In the packaging process, you need to add some relevant information, such as the title of the file, the artist's name, copyright notice, image, URL to obtain the license, and other additional information. The packaged content and license are separate and reach the user terminal over the network. To use the packaged media content file, the user must be authorized to use the license. The key information contained in the license can be used to decrypt the content for viewing, and the license is bundled on the client's computer and cannot be shared.
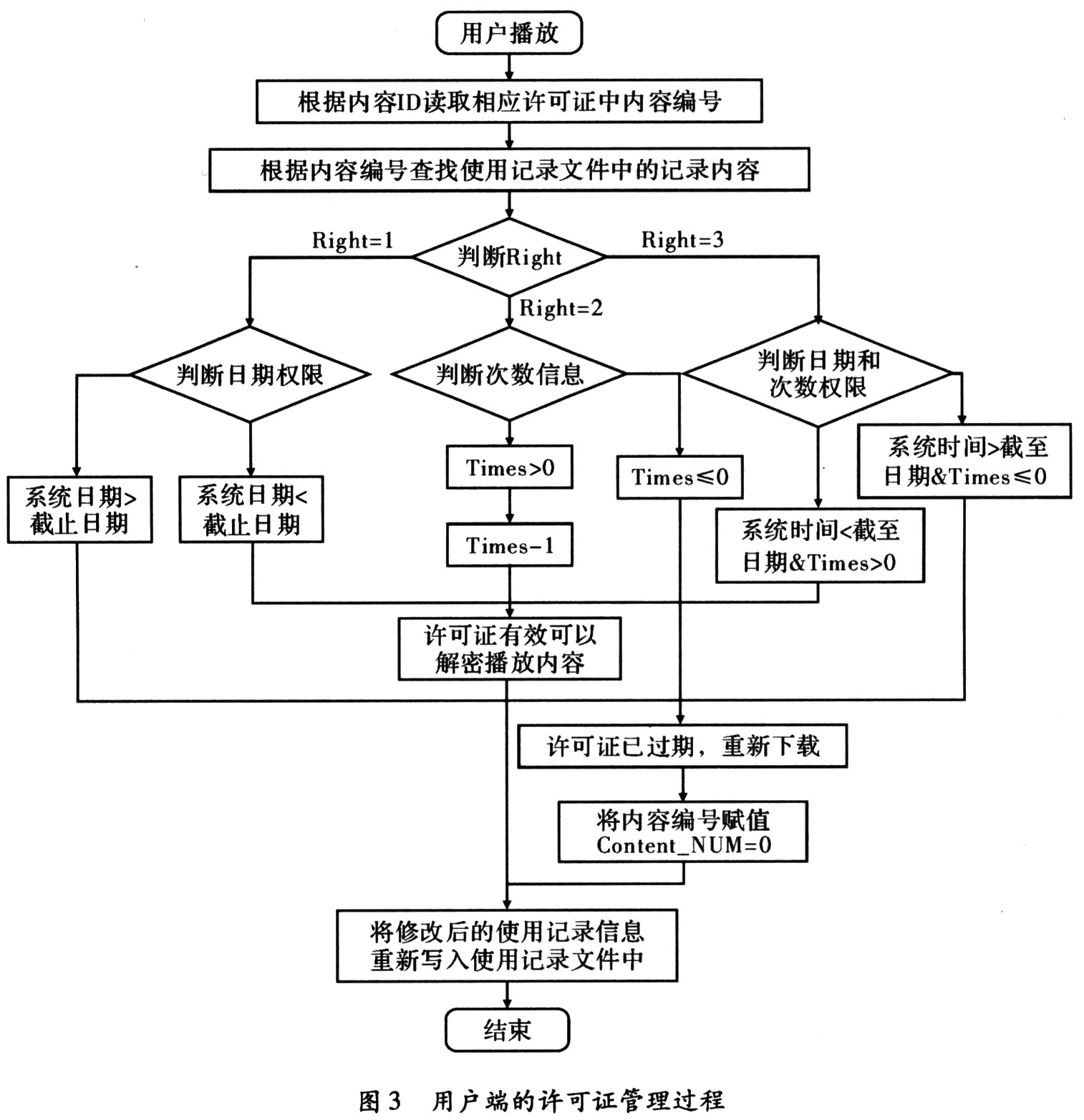
2 Traditional license verification and management process When a user plays a packaged media file for the first time, the process of detecting the license is automatically started. If such an authorized license is not detected on the user's computer, the web browser opens the registration page of the license authorization service center of the content file, prompting the customer to input some user information registered by the content provider in advance. Once the validity of the user input is verified, an authorized license that cannot be shared is issued.
The implementation process in the text defines a simple license structure variable in C language, including: user public key information (384.bit), content ID (160 bit), content number (16 bit), permission information (8 bit), use Number of times (8 bit), expiration date (24 bit), issue date (24 bit), AES key (576 bit) encrypted by Ecc, server public key certificate ID (64 bit), HASH digest value (192 bit), Signature value (384 bit).
After receiving the license, the client will perform the license verification and management process according to the following process. The client should first verify the correctness of the user's public key certificate, then HASH the information in the obtained license, and verify the security, reliability and integrity of the license against the hash value in the license. Finally, you need to verify the signature value of the license to determine the legitimacy of the server that issued the license.

Information to be verified:
(1) The user's public key information (extracted from the user's public key certificate);
(2) Hash hash summary value;
(3) Digital signature value.
After the license verification is completed, the user rights information and the license validity period need to be written into the client's license management record file. When the user needs to play the packaged media file again next time, the license detection program will first check the license. If there is any relevant authorization information of the media file in the license management record file, and verify the validity of the license authority, proceed to the next step. If the information about the media file in the license management log file exists and is valid, the client does not need to connect to the license authorization server to apply for a license again, otherwise it will need to reapply. If the corresponding content exists in the license management log file, the permission information in the change log file is required after verifying the valid permission.
The usage log file contains:
(1) Content_NUM content number (16 bit);
(2) Right permission information (8 bit);
(3) End-Date deadline (24 bit);
(4) Times usage (8 bit).
An expired license exists after the user plays the content, and there is an expired usage record information in the usage log file. After determining that the usage record expires, the content number will be assigned to 0. When the next use record information is written, firstly, it is found whether there is a record item with the content number 0, and if it exists, the usage record information is overwritten with the original content; If it exists, add the usage record information at the end of the file.
3 Second generation digital copyright protection mechanism XrML
As a second-generation digital copyright protection management mechanism description language, xrML is a branch of the XML language (short for eXtensible MarkupLanguage, meaning extensible markup language), because it inherits the advantages of XML language and is convenient and simple to describe and powerful. It is more and more widely used for scalability, and provides more powerful technical support in digital rights management.
The usual rights management technology protects and controls the contents of the file by pre-setting certain rules and policies, and can perform various important content operations, such as simple viewing, printing, editing, and sharing. But this proprietary form of digital rights management has made it difficult to share content with other forms. Just like the implementation of the C language structure implementation license mentioned above, the permissions and contents that can be given are very limited, it is difficult to implement expansion for complex systems, and it takes up more system space, which is more limited in the client space. There will be serious problems in the system. However, XrML lists the access and usage policies for digital content in a licensed form that defines who can access the content, how to protect and distribute the content, and controls detailed usage rights to perform certain operations, such as authorized printing and time licensing. Wait.
XrML2. The O core concept includes "license, grant, princi-pal, right, resource and condition".
The important top-level structure in XrML 2.0 is a li-cense. Conceptually, a license can be understood as a container for grant. A basic license should include the following structure:
(1) granting someone a specific right to a data source under certain circumstances;
(2) Authenticate a person before granting his or her rights;
(3) A variety of related information.
Grant is an important element used in a license to provide permission to a grantee to communicate a license to a specific data source. Structurally, it has the following characteristics:
(1) Information of the grantor of the right;
(2) information on the rights granted;
(3) The rights that the user can exercise or the information of the data source that can be obtained;
(4) The specific conditions that must be met before the exercise of rights.
The Principal element is used to describe the rights holder's information. It supports the following three definition methods:
(1) A granted right user needs to meet multiple authentication conditions, all of which must be valid before they can be granted the right to execute the data source;
(2) Keyholder, which means that the right is granted to the holder of the special key;
(3) Other definition types.
The main structure of XrML2.0 also includes the fight, resource and condition elements. The right element is used to describe the user's right to operate the data source; the resource element is used to describe the data source; the condition element is used to define the conditions for the user to exercise the rights. These main elements form the main structure of XrML 2.0, and they collectively describe the standardized language in digital authorization.
Of course, a simple license file can be generated through the above various structures, and the specific user is given a simple use right. However, in order to ensure that the user is confident that the license is legal and correct, it must also be digitally signed after the license file.
XML signatures can be used to ensure that the content in the XML document has not changed. If used in conjunction with XML encryption, the received data is guaranteed to be sent, and outsiders cannot read the encrypted content.

Between the s02 line and the s12 line in the above list is the Signedlnf element, which is the actual signature information. The core verification of Signedlnfo consists of two necessary processes: signature verification for Signedlnfo and verification of each Reference digest within Signedlnfo.
On line s03, CanonicalizationMethod identifies an algorithm that is used to normalize the SignedInfo element, which is then abstracted as part of the signature operation.
On line s04, SignatureMethod refers to the algorithm used to convert the normalized SignedInfo to Signaturevalue. It is a combination of a key-related algorithm and a digest algorithm (here, DSA and SHA-1) that is signed by the algorithm to resist attacks, which are based on replacement with less efficient algorithms.
Each of the Reference elements of s05-s11 includes a digest method and a digest value calculated for the identified data object. It may also include generating input conversions for summary operations. The signature of a data object is performed by calculating its digest value and signing the value. The signature is later checked by reference and signature verification, which recreates the digest value and ensures that it matches the content in the data object.
On line s05, this optional URI attribute of Reference identifies the data object to be signed. In a Signature, you can omit this attribute for at most one Reference.
S09-s10 DigestMethod is an algorithm applied to data to generate DigestValue. The signature of DigestValue is the mechanism for binding the resource content to the signer key.
On line s13 is the SignatureValue element itself, which is outside of SignedInfo, which is outside the signature part, but the algorithm used to calculate SignatureValue is included in the signed message.
Between line s14 and line s16 is the Keylnfo element (which is optional), which indicates the key used to verify the signature. The identification mechanism can include a certificate, a key name, and a key agreement algorithm.
The signed XrML license can be sent to the client through the license server. The client only needs to extract the content through the XML parser to verify the legality of the sender of the license and extract the media file content key from it. The media file to be played is decrypted and viewed. However, the client also has a license verifier, which needs to verify and judge the permissions granted by the license, and gives the user the corresponding authority.
4 Conclusion By comparing the use of C language and XrML to realize the management of digital TV video on demand digital license, it can be seen that the traditional rights management method is difficult to expand and realize complex, but it requires relatively simple rights protection and cannot Providing a higher implementation platform is a relatively straightforward approach. Due to the emergence of the second generation of digital rights protection system, xrML has been widely used, and there are parsers and validators developed in C++ and Java under Linux and Windows environments. The experiments in this article are all implemented in the Windows environment, but with the emergence of these parsers, it is easy to apply in the Linux operating system environment. And for the traditional digital rights management scheme, only the application of the C language structure to define part of the necessary information and simple digital rights, there are specialities and limitations.
Due to the popularity of the Internet, digital copyright protection has become more and more important, attracting more and more people's attention. Whether it is e-books, music, movies, mp3 and other online media files will face the threat of copyright, with its good scalability and simple design, XrML language will become the industry standard for digital rights management.
We combine the Bluetooth speaker with RGBW Light, one switch easy control four lighting modes: warm white lighting mode, no lighting mode, dazzling lighting mode, RGB lighting mode. High-quality speaker with loud, clear sound, combine with color lighting, can be used in the bedrooms, gardens, and swimming pools.
We offer two kinds of Bluetooth speakers, one is with plastic sticker, it can be used in garden, waterproof index is IP44; the other one is with waterproof plug, it can be used around swimming pool, waterproof index is IP67.
Product parameters
Product dimension: Dia 155mm x H 45mm
Material: ABS+PC
Weight: 300g
LED Color: RGB+Warm White
LED Power: 0.5W
Speaker Power: 5W
Lamp Current: 15-20mA
LED Qty: 8pcs RGB lamp beads+4pcs Warm White lamp beads
Battery Capacity: 3.7V, 1000mA (Li battery included)
Protocol: Bluetooth 4.1-CSR
Charging type: by a USB charger
Control Distance: 10m ( No obstacles)
Charging Time: 1.5 hours
Continue Use Time: 3-5 hours
Packing: Each in a color box
Warranty: 1 Year
Certification: CE (EMC,RED) ,ROHS, SCC, BQB,FCC
Suitable Occasions: Indoor and outdoor, can be used in the swimming pool as a Floating Speaker With Light
Bluetooth Speaker With Light,Bluetooth Speaker Light,Bluetooth Mesh Light, Bluetooth Wireless Speaker Light
Ningbo Homey Photoelectric Tech. Co., Ltd , http://www.linkuphome.com