Yesterday's article talked about the huge threat of hackers to driverless. Today we will talk about the attitude of the car factory to hackers.
While half of the industry respondents believe that hackers will target cars as targets, only 54% of respondents said their companies have prioritized security.
Recently, the US government's auto safety regulations authorities have issued a set of "cybersecurity guideline" (reference link) for automakers. US Transportation Secretary Anthony Foxx said that cybersecurity is the top priority for the department. issue.

Obviously, the US government expects to pre-empt potential attacks against vehicles before networked vehicles face cybersecurity threats; the authorities are concerned that cybersecurity issues may cause irreparable damage to highly automated vehicles in the future, but don't care too much about such concerns. It turns out that some experts in the automotive industry do not believe that hackers are interested in attacking cars.
The above observations are evident in a survey conducted by Ponemon InsTItute, an independent security technology research organization that stated that the goal of the survey was to collect information on the state of safety practice in the industry; the survey collected 500 respondents. In the questionnaire, all respondents were directly involved in automotive software development, with 44% of the respondents coming from the car factory and the rest working on automotive component suppliers.
Gene Carter, director of product management and marketing at Security InnovaTIon, one of the sponsors of the Ponemon survey, said that in view of the number of car network security incidents that have caught the attention of the public in the past 12 months, people may expect the automotive industry's attitude toward cybersecurity. There is a revolutionary change; but the survey found that automakers and component suppliers did not prioritize cybersecurity as a vehicle development priority: "The auto industry has a long way to go before it is fully prepared to respond to cybersecurity. Going."
According to feedback from 500 respondents, only 52% of people think that hackers will take the initiative to target the car, which is a slight increase from the previous year's survey results of 44% - whether the Jeep car was successfully invaded by hackers, The car factory Chrysler recalled 1.4 million cars in 2015, and did not sound the alarm in the industry? It doesn't seem to be.
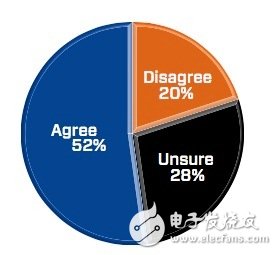
Proportion of respondents who believe that hackers will list cars as targets (Source: Ponemon InsTItute)
While half of the industry respondents believe that hackers will target cars as targets, only 54% of respondents said their companies have prioritized security. In addition, less than half (42%) of respondents indicated that their company incorporated stringent security requirements into product development programs such as design, implementation, and testing.
Carter said that even some industries have begun to accept the reality that car hackers will really become a threat: "The behavior of automakers and component suppliers has not changed in response to this increasingly significant doubt."
Who should take responsibility?Ponemon's survey also asked respondents, who should ultimately be responsible for ensuring safety during the car development process? Carter explained: "We asked this question because the answer shows that car manufacturers are giving priority to promoting cybersecurity."
The survey results show that respondents believe that the role of the most responsible for ensuring security in the car development process is: Chief Information Officer (CIO, 22%), Chief Information Security Officer (Chief informaTIon Security Officer, 17%), product Quality Assurance (18%), Development Engineer (12%) and partners (11%).
However, only one in five (19%) of respondents believe that no one should assume all responsibility for ensuring safety during the car development process: “This is a warning, meaning no one is responsible.â€

Who is responsible for ensuring safety (Source: Ponemon Institute)
The survey also showed that only 15% of respondents felt that security was fully integrated into the automotive product development process; about half (47%) of respondents believed that security was added at the end of the development process. of. Not only is security not integrated within the product, the survey also found that more than half (55%) of companies did not include security architecture in the supply chain and partner network.
Carter's observation is: “Thinking security as an add-on clearly shows that security is not a priority for many vendors;†he said, to achieve the best results, network security must be listed at the earliest stages of vehicle or automotive component development. It is a must.
The challenge of connected car securityWhen asked about the main challenges in securing car software, the list of respondents included: lack of technical staff (65%), implementation pressure (65%), insufficient resources (58%), Lack of a clear enterprise application security strategy (43%), lack of formal security requirements (34%), time limits (18%), and expenses (11%). The above results are similar to the results of 2015. Only because of the implementation of the pressure, the 54% of the previous year has increased significantly.
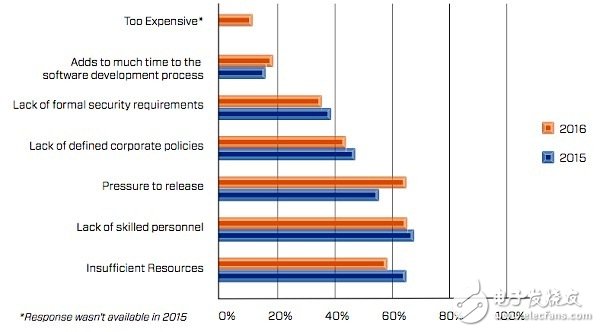
Ensuring the Challenges of Automotive Software Security (Source: Ponemon Institute)
In all fairness, in the practice of automotive network security, the automotive industry faces an almost insurmountable challenge because of the dominant technology; Carter said, for example, the current CAN bus and OBD-II functions hinder the car from becoming more The direction of security is developing, and the CAN bus that is everywhere in the car is not a good platform for network security. It takes a lot of investment to change, but maybe the car manufacturer thinks this risk is too great.
Obviously, the industry's worries about car hackers have improved, but the response is still too weak; curiously, the survey results show that car manufacturers' awareness of the safety weakness of cars has increased by nearly 10%, but automotive component suppliers. The reaction is slower.
Carter guessed this because: "The operating profit of component suppliers is really very low, and safety means cost, unless car manufacturers ask them to add security, and they are willing to invest in it; however, to change the supply of automotive components The mentality of the business may be very difficult."
What tools are used to achieve security?Ponemon's survey also found that the automotive industry has begun to use a variety of security tools: more than half (53%) of respondents said they are already using the secure boot feature, and 44% said they use encryption Communication, 42% use encrypted data storage, and 39% use endpoint authentication.
The survey concluded that “although the trend has an encouraging effect, the proportion of vendors using safety tools and technologies is still low, and only 24% of respondents said that the company uses high-level risk assessment such as Threat Modeling. Tools, and this is a proven way to find security holes in the product development process, which is the most effective (saving) fixed tool."

System security features used by car manufacturers (Source: Ponemon Institute)
The five major automotive network security objectives outlined by the National Highway Traffic Safety Administration (NHTSA) include:
• Promote and share automotive network security knowledge; • Set industry-based best practices and voluntary standards; • Develop software that protects against car hacking; • Determine the feasibility of minimum performance standards; • Collect research data to All industries and NHTSA can be used to develop strategies and laws.
Those that are not necessarily the most stringent network security targets that NHTSA imposes on automakers are actually relatively loose, open, and fluent; NHTSA Director Mark Rosekind said that in an environment where technology and network security continue to change, only a single solution is Not enough, all relevant players should continue to act, adapt and run in front of the malicious.
Some US congressmen criticize NHTSA's guiding principle as being too friendly to the auto industry, because if today's cars are wheels-based computers, they need mandatory standards rather than voluntary guidelines to ensure that cars are not hacked or allowed. People’s lives and privacy are exposed to danger.
Solid-state capacitors / Motor starting capacitors
Solid - state capacitors are all called: solid - state Aluminum Electrolytic Capacitors.It with the ordinary capacitance (that is, the liquid aluminum electrolytic capacitors) the biggest difference is that use different dielectric material, liquid aluminum capacitor dielectric material as the electrolyte, and solid-state capacitor dielectric material is conductive polymer materials.Solid-state capacitors / Motor starting capacitors
Solid-state capacitors / Motor starting capacitors,Solid-State Capacitors,Solid-State Small Size Capacitors,Solid-State Low Impedance Capacitors,Long Life Solid-State Capacitors
YANGZHOU POSITIONING TECH CO., LTD , https://www.yzpstcc.com